RapperBot is a distressing new application that can ruin your day if it happens to get onto your server. It infiltrates SSH servers and causes all sorts of mayhem. It changes passwords, adds users, and does many other terrible things. If you run an SSH server at home or for business and are concerned about someone infecting it with RapperBot, then continue reading this article as it will give you some tips on how to protect against RapperBot and a few strategies for confirming that you have a RapperBot infection on your hands.
How RapperBot works
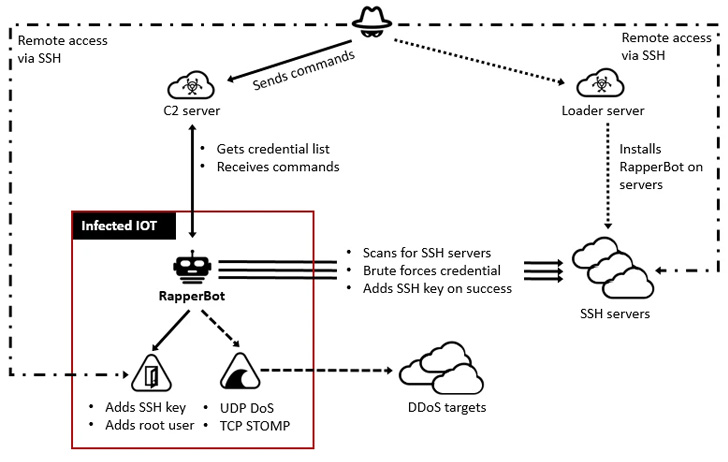
RapperBot heavily reuses parts of the Mirai source code and implements the same functionality as its predecessor. However, it also includes new features such as an additional port for reporting valid credentials to the C2 server (48109) and self-propagating via a remote binary downloader post-compromise.
How to protect against RapperBot
The best way to protect yourself from RapperBot is to use secure passwords with at least 12 characters that include numbers, capital and small letters, and symbols. You should also use a private and public key with your SSH server so that you can access it safely from anywhere. In addition, try to avoid exposing your SSH server to the internet in general—the less vulnerable it is, the better!
If you think your system is infected
If you’re worried that your SSH server has been compromised by RapperBot, there are a few things you can do to check.
- First, check the logs. If you see any suspicious logins from IP addresses outside of your organization, or from the same IP address multiple times in a row, this could be a sign that someone has gained access to your server.
- Verify that the authorized_keys file has not been altered.To do this, you will need to:
a. Navigate to the directory where your authorized_keys file is located.
b. Open the authorized_keys file in a text editor such as Notepad++ or Nano.
c. Verify that the public key listed under “pub” matches your original public key as well as the public key of any other user with access to your account. If there are any discrepancies between these keys, it is likely that someone has modified your authorized_keys file, and you should immediately change all of your passwords for this account, as well as for any other accounts with which you shared any passwords through RapperBot. Here is what your authorized_key file will look like if you have been compromised.
ssh-rsaAAAAB3NzaC1yc2EAAAADAQABAAACAQC/yU0iqklqw6etPlUon4mZzxslFWq8G8sRyluQMD3i8tpQWT2cX/mwGgSRCz7HMLyxt87olYIPemTIRBiyqk8SLD3ijQpfZwQ9vs Hc47hdTBfj89FeHJGGm1KpWg8lrXeMW+5jIXTFmEFhbJ18wc25Dcds4QCM0DvZGr/Pg4+kqJ0gLyqYmB2fdNzBcU05QhhWW6tSuYcXcyAz8Cp73JmN6TcPuVqHeFYDg05KweY qTqThFFHbdxdqqrWy6fNt8q/cgI30NBa5W2LyZ4b1v6324IEJuxImARIxTc96Igaf30LUza8kbZyc3bewY6IsFUN1PjQJcJi0ubVLyWyyJ554Tv8BBfPdY4jqCr4PzaJ2Rc1J FJYUSVVT4yX2p7L6iRpW212eZmqLMSoR5a2a/tO2s1giIlb+0EHtFWc2QH7yz/ZBjnun7opIoslLVvYJ9cxMoLeLr5Ig+zny+IEA3x090xtcL62X0jea6btVnYo7UN2BARziis Zze6oVuOTCBijuyvOM6ROZ6s/wl4CQAOSLDeFIP5L1paP9V1XLaYLDBAodNaUPFfTxggH3tZrnnU8Dge5/1JNa08F3WNUPM1S1x8L2HMatwc82x35jXyBSp3AMbdxMPhvyYI8v 2J1PqJH8OqGTVjdWe40mD2osRgLo1EOfP/SFBTD5VEo95K2ZLQ== helloworld - Monitor for outgoing traffic on port 48109 to these following C2 IP addresses.
31[.]44[.]185[.]235
2[.]58[.]149[.]116
194[.]31[.]98[.]244
185[.]225[.]73[.]196 - Monitor for incoming traffic from the following IP addresses that house the malware and then downloads to your system.
hxxp://31[.]44[.]185[.]235/x86
hxxp://31[.]44[.]185[.]235/mips
hxxp://31[.]44[.]185[.]235/arm7
hxxp://2[.]58[.]149[.]116/arm
hxxp://2[.]58[.]149[.]116/spc
hxxp://2[.]58[.]149[.]116/mips
hxxp://2[.]58[.]149[.]116/x86_64
hxxp://2[.]58[.]149[.]116/ssh/arm7
hxxp://2[.]58[.]149[.]116/ssh/mips
hxxp://2[.]58[.]149[.]116/ssh/x86
hxxp://2[.]58[.]149[.]116/ssh/spc
hxxp://194[.]31[.]98[.]244/ssh/new/spc
hxxp://194[.]31[.]98[.]244/ssh/new/x86
hxxp://194[.]31[.]98[.]244/ssh/new/mips
hxxp://194[.]31[.]98[.]244/ssh/new/arm7
hxxp://194[.]31[.]98[.]244/ssh/new/arm
hxxp://194[.]31[.]98[.]244/ssh/new/x86
hxxp://194[.]31[.]98[.]244/ssh/new/mips
hxxp://194[.]31[.]98[.]244/ssh/new/arm7
hxxp://194[.]31[.]98[.]244/ssh/new/arm
hxxp://185[.]225[.]73[.]196/ssh/new/arm
hxxp://185[.]225[.]73[.]196/ssh/new/arm7
hxxp://185[.]225[.]73[.]196/ssh/new/mips
hxxp//185[.]225[.]73[.]196/ssh/new/x86
Conclusion
Using public key authentication will increase the amount of time it takes for a hacker to get into your account. However, that added security also requires more work on your end, like generating a public/private key pair and configuring SSH to use them rather than passwords. But in our opinion, it’s worth the extra effort. Of course, you’ll also probably want to enable login monitoring on the server, so you can be notified of any unauthorized logins.
These are just a few suggestions that should be considered after the breach of security from RapperBot. We strongly recommend (especially for those who manage a SSH server) to check the list and apply any precautions deemed necessary.
